What is MTA-STS and how does it Improve Email Security?
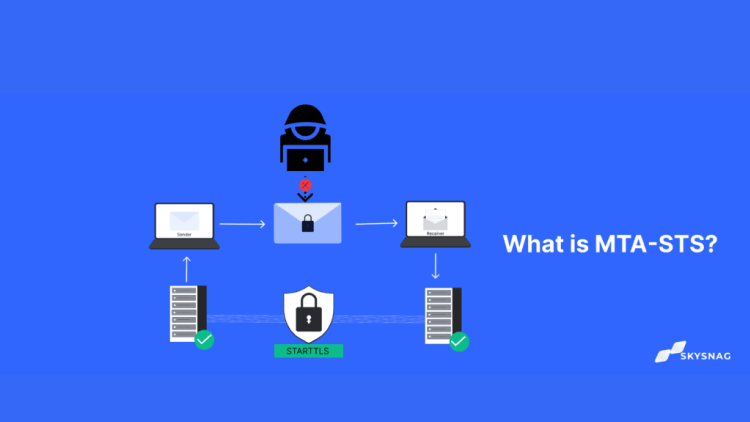
Mail Transfer Agent Strict Transport Security (MTA-STS) is a security policy for SMTP servers that is specified in RFC 8461. The policy allows an SMTP server to declare that it supports TLS and to specify a set of security policies that clients must use when connecting to the server. The policy can be used to require that clients use TLS with a specific set of cipher suites, to require that clients verify the server’s certificate, or require that clients verify the server’s identity by checking for a specific DNS record.
The objectives of MTA-STS
The Mail Transfer Agent Strict Transport Security standard is intended to provide a secure method for exchanging security tokens between security token services (STS) and relying parties. The standard is also intended to promote the use of security tokens in general, by providing a consistent way for STSs to issue and exchange them.
How Does MTA-STS Improve Your Email Security?
Mail Transfer Agent Strict Transport Security is the suggested email authentication standard to reduce SMTP security issues. To enable MTAs to transmit emails securely, it enforces TLS.
As a result, it will only permit mail to come from MTAs that support TLS encryption and mail to travel to MX sites that support TLS encryption.
If an encrypted connection cannot be established between two SMTP servers that are in communication, the email is not sent and is instead transmitted across an insecure connection.
What conditions must be met for MTA-STS?
The following conditions must be met before deploying this security protocol:
- A valid SSL certificate must be installed on the server.
- The server must be configured to support TLS 1.2 or higher.
- The server must be configured to support the MTA-STS policy.
In order to see the performance of your domains and the success/failure rate of your MTA-STS policies you should implement TLS reporting. The important insight will be generated to ensure no interruption in mail flow
How does MTA-STS work?
MTA-STS is a policy enforcement mechanism that allows an email receiving domain to declare via DNS that it enforces STARTTLS for inbound email and provides a mechanism for senders to discover that policy. It uses standard TLS certificate validation processes and DNS record discovery mechanisms to validate policies and enforce STARTTLS.
Enable MTA-STS to your domain
To enable MTA-STS on your domain, you require a DNS TXT resource record with the following:
- “v” The protocol version, which authenticates the value STSv1 at this time.
- “id” is an alphanumeric string of 1 through 32 characters used to track policy modifications. Modify the string when changes are made to your MTA-STS file.
Here is an example of such a record:
_mta-sts.example.org. IN TXT “v=STSv1; id=202104012135;”
Use our Free MTA-STS Record Checker tool to validate your MTA-STS records.
Conclusion
Skysnag makes your life a lot easier by managing everything for you in the background. With the aid of our automated software, you can quickly and easily set up MTA-STS in your business. Protect your business email from being compromised by allowing receiving emails to be sent to your domain over a TLS encrypted connection preventing MITM attacks. Get started with Skysnag by signing up using this link for a free trial today.