What is an Impersonation Attack? Everything you need to know in 2022
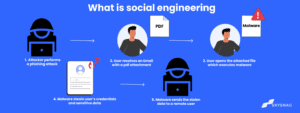
Businesses that rely on conventional anti-phishing equipment are finding that phishing is increasingly turning into an undetectable threat. An impersonation attack is a perfect example of a modern phishing scam since they are targeted, clever, and depend more on social engineering than on malicious attachments or links.
Impersonation attacks come from legitimate emails which might resemble and look like the actual email address. With Skysnag’s automated SPF, DKIM, and DMARC email providers are certain that only legitimate emails are delivered to users’ inboxes and that any suspicious or malicious emails are blocked. This helps to protect your users from potentially harmful or fraudulent emails and makes it more difficult for scammers and phishers to target email users.
Everything you need to know about impersonation attacks, their types, how to recognize them, and how to protect your organization against them are discussed in this article. We’ll start with the basics but feel free to jump ahead with the links below.
Table of Contents:
- What is an Impersonation Attack?
- What are the types of impersonation attacks?
- How does an Impersonation attack happen?
- How to detect impersonation attacks
- Protect your Organization against Impersonation
- Conclusion
What is an Impersonation Attack?
An impersonation attack is a type of cyber attack where an attacker impersonates another user or entity in order to gain access to information or resources that they would not normally have access to. Impersonation attacks are often used in phishing scams and social engineering attacks.
Here’s an email impersonation attack example
As you can see above, the differences between the two emails are minimal and easy to miss, especially if you receive hundreds of emails every day. Attack emails impersonating legitimate emails may resemble and appear to be the real thing.
What are the types of impersonation attacks?
There are three main types of impersonation attacks:
Email Spoofing
This type of attack involves the attacker pretending to be someone else in order to gain access to information or resources that they would not otherwise have access to.
Phishing
This type of attack involves the attacker sending emails or other messages that appear to be from a legitimate source in order to trick the recipient into revealing sensitive information or clicking on a malicious link.
Social engineering
This type of attack involves the attacker using psychological manipulation to convince the victim to perform an action that will allow the attacker to gain access to information or resources.
How does an Impersonation attack happen?
Impersonation is when a malicious attacker poses as a trustworthy customer or service in order to access secured data. To deceive people into believing they are who they claim to be, an attacker only needs to obtain sufficient information about a reliable user or service. The attacker will then attempt to persuade their target to divulge private data that is ordinarily secured by security measures.
Attackers frequently attempt impersonation attacks via email or other means of communication.
How to detect impersonation attacks
Skysnag provides an easy-to-configure, all-in-one solution to protect your email domain immediately. Our automated domain tools help to successfully monitor every aspect of your email authentication and enforce powerful and effective protection from impersonation attacks. To stay one step ahead of cybercriminals, there are a few basic things you should always be aware of.
Sense of Urgency.
The majority of impersonation attempts ask or demand that the target take quick action. Some impersonation emails may make dire threats if the recipient doesn’t take action right away. This is done to stop the employee from checking things twice before acting.
Emphasis on maintaining privacy.
Some impersonation assaults will make the claim that the behavior is related to a secret project or confidential development that shouldn’t be discussed with coworkers or immediate superiors.
A request for financial assistance or confidential information
Any request for a money transfer, the release of confidential financial information, personnel records, or intellectual property should be supported by numerous channels of verification.
Modified email addresses
For instance, if you receive an email asking you to check-in and update your account information from someone posing as “Paypal,” but the email address is actually “[email protected],” this may be an impersonation assault. But keep in mind that this is only useful against attempts at email spoofing. Keep a look out for other warning flags because account takeover is harder to detect than other frauds.
Protect your Organization against Impersonation
Educate your team
Organizations need to understand how crucial cybersecurity training is to safeguard against this kind of attack. Employee security awareness training that informs them of the signs of impersonation attacks, how to stop them and the amount of harm that a successful attack may bring should be covered in the training. Assuring that all new hires receive training to help them recognize impersonation attacks and know what to do if their accounts are compromised is key.
Secure your email
Skysnag has developed powerful automated encryption tools for you that keep your email contents and their attachments safe, and are simple to employ, while also delivering digital signing and state-of-the-art verification processes.
Deploy Email Authentication Protocols
A good way to start out is by deploying SPF.
Skysnag’s automated Sender Policy Framework solution will certify that the IP used for sending an email has the right to do so. It prevents fraudulent use of your domain name and prevents third parties from pretending to be you.
DomainKeys Identified Mail, or DKIM,
Our automated DKIM solution helps you to confirm the sender and content of emails while examining email messages’ origin and content in an effort to lower the amount of spam, phishing, and other harmful emails.
Domain-based Message Authentication, Reporting, and Conformance (DMARC
Create a Skysnag account to generate your DMARC record
Skysnag’s automated DMARC strengthens protection against phishing and spoofing by confirming that an email message came from the domain it claims to have come from. Skysnag generates DMARC reports for you that aid in investigating potential security problems and identifying potential risks from impersonation attacks.
Conclusion
Skysnag’s automated DMARC solution strengthens protection against phishing and spoofing by confirming that an email message came from the domain it claims to have come from. Skysnag generates DMARC reports for you that aid in investigating potential security problems and identifying potential risks from impersonation attacks. Get started with Skysnag and sign up using this link.