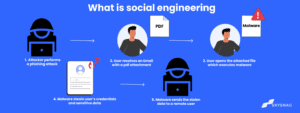
In the ever-evolving world of cybersecurity, targeted attacks like whaling and spear phishing pose significant threats to organizations of all sizes. These sophisticated social engineering tactics exploit human vulnerabilities, but they differ in their approach, targets, and potential impact. Understanding the key differences between whaling and spear phishing is crucial for businesses to defend against these cyber threats effectively.
What is Spear Phishing?
Spear phishing is a targeted form of phishing where attackers focus on a specific individual or organization. Unlike broad phishing attempts that target large numbers of people with generic messages, spear phishing involves a high degree of personalization. Attackers gather information from social media, company websites, and previous breaches to craft messages that appear legitimate to the recipient.
How Spear Phishing Attacks Work
- Target Identification: Attackers select a specific individual, often someone with access to sensitive information or financial resources.
- Message Personalization: Using collected data, they create a convincing email or message that seems to come from a trusted source.
- Attack Execution: The target receives the message, which typically includes a malicious link, attachment, or request for sensitive information.
- Exploitation: If the target falls for the scam, the attacker gains access to valuable data, financial accounts, or internal systems.
Spear phishing attacks often target employees at various levels, including IT staff, finance departments, and mid-level managers.
What is Whaling?
Whaling is a specific type of spear phishing that targets high-profile individuals, such as CEOs, CFOs, and other senior executives. These attacks are generally more sophisticated and carry higher stakes due to the target’s authority and access to sensitive information.
How Whaling Attacks Work
- Executive Targeting: Attackers focus on senior executives or other high-ranking individuals within an organization.
- In-Depth Research: To deceive these high-profile targets, attackers conduct extensive research to craft highly convincing and authoritative messages.
- Precision Attack: The attack often involves urgent, high-stakes business matters, such as requests for large financial transactions, sharing of confidential data, or downloading of malware.
- High-Stakes Exploitation: Due to the significant power and access of the target, successful whaling attacks can result in catastrophic financial losses, data breaches, and severe reputational damage.
A Side-by-Side Comparison
Understanding the differences between whaling and spear phishing is essential for implementing effective cybersecurity measures. Here’s a comparison of the two:
| Aspect | Spear Phishing | Whaling |
|---|---|---|
| Target Audience | Employees at various levels within an organization | Senior executives and high-ranking officials |
| Sophistication | Varies; often involves personalized attacks using readily available information | Highly sophisticated; involves in-depth research and convincing, authoritative messages |
| Impact | Limited to the target’s access and authority | Potentially catastrophic due to the target’s high-level access and decision-making power |
| Common Attack Methods | Fake invoices, fraudulent login pages, requests for sensitive information | Mimics legal documents, executive requests, or high-level communications |
| Goal | To gain access to sensitive information or financial resources | To execute large financial transactions, steal confidential data, or deploy malware |
Defending Your Organization
Given the targeted nature of both whaling and spear phishing, organizations need to adopt a multi-layered approach to defense:
- Advanced Email Security: Implement robust email filtering systems and authentication protocols like DMARC, SPF, and DKIM to reduce the risk of email spoofing.
- Employee Education and Training: Regular training sessions to help employees recognize phishing attempts, with a special focus on high-level executives.
- Multi-Factor Authentication (MFA): Enforce MFA, particularly for accessing sensitive data or authorizing transactions, to add an additional layer of security.
- Executive Protection: Provide tailored security training and support for executives, including personalized phishing simulations and secure communication channels.
- Incident Response Plan: Ensure that a comprehensive incident response plan is in place to quickly address any successful phishing or whaling attempts.
Conclusion
While whaling and spear phishing both pose serious threats to organizations, the stakes in whaling attacks are particularly high due to the seniority of the targets involved. By understanding the differences between these two types of cyber threats and implementing targeted defenses, organizations can better protect themselves from potentially devastating consequences.
As cybercriminals continue to refine their tactics, staying informed and vigilant is key to safeguarding your organization’s most valuable assets. Get started with Skysnag to automate DMARC enforcement and secure your organization’s email communication.

Check your domain’s DMARC security compliance
Enforce DMARC, SPF and DKIM in days - not months
Skysnag helps busy engineers enforce DMARC, responds to any misconfigurations for SPF or DKIM which increases email deliverability, and eliminates email spoofing and identity impersonation.