Spear phishing vs Phishing. Know the difference!

Phishing attempts are nothing new in the online world, and scammers have been infiltrating inboxes for years. Phishing assaults have dramatically increased as the internet has grown. 19,369 Business Email Compromise (BEC) and Email Account Compromise (EAC) allegations were received by the FBI’s IC3 in 2020, resulting in a loss of over 1.8 billion (Internet Crime Complaint Center).
A phishing attack’s main objective is to gain access to sensitive information and utilize it improperly!
In order to defend oneself against these assaults, Skysnag has developed the right DMARC tools to help protect you from phishing attacks.
In this article, we will be looking at the differences between spear phishing vs phishing. We’ll start with the basics but feel free to jump ahead with the links below.
Table of contents
- What is Spear Phishing?
- Techniques used in a Spear Phishing attack:
- What is phishing?
- What are 3 signs of a phishing email?
- What are the differences between Spear phishing VS Phishing?
- Ways to protect yourself against Phishing and Spear Phishing Attacks?
- How Skysnag can protect your organization from Spear-phishing and Phishing attacks.
What is Spear Phishing?
A specific person or business is the target of a spear-phishing assault, which is a sort of phishing attack.
To make the email look more credible, the attacker will typically gather information on the target beforehand.
Social media, government databases, and other sources are all good places to look for this information.
Techniques used in a Spear Phishing attack:
The two commonly used Spear Phishing attacks include:
Whaling:
This is an attack directed at company executives who have access to sensitive information or who have the authority to authorize substantial cash transfers.
CEO fraud:
The fraudster impersonates a company’s CEO coercing the victim into performing unlawful action
What is phishing?
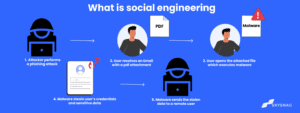
Phishing is a kind of internet scam in which fraudsters assume the identity of a trustworthy company or person to fool victims into divulging personal information like credit card numbers, passwords, or account login information.
Links to malicious websites that are created to look like the official website of the company the email purports to be from are frequently included in phishing emails. When victims click on these links, a bogus website is loaded and a form asking for personal information is shown.
Once this information is obtained, criminals exploit it to perpetrate fraud or identity theft.
What are 3 signs of a phishing email?
1. The email has poor grammar and spelling mistakes.
2. The email is from an unknown sender.
3. The email contains a sense of urgency.
What are the differences between Spear phishing VS Phishing?
Because they apply the same criteria, spear-phishing and phishing may be confused.
That is untrue, though. Despite the fact that they are both types of social engineering, they differ significantly from one another. Let’s look at how they differ.
Spear phishing is a targeted phishing attack where the attacker attempts to gain information from a specific individual or organization, while phishing is a general phishing attack where the attacker attempts to gain information from anyone who responds to the email.
Spear phishing might be considerably riskier than regular phishing because of their hyper-targeted nature. A spear-phishing message’s familiar tone and content make it harder for the average user to recognize it, raising the threat level of this kind of cyberattack.
Ways to protect yourself against Phishing and Spear Phishing Attacks?
You can take the following actions to safeguard yourself from spear-phishing and phishing attacks, as well as those of others:
- Be cautious if an email, text, or social media message is sent by an unidentified sender.
- Avoid clicking on links or opening attachments from unidentified senders.
- Any email, text, or social media post with typos or grammatical problems should raise suspicions.
- Any email, text, or social media message asking you to send personal or sensitive information should be avoided.
- Before taking any further action, get in touch with the sender of an email, text message, or social media communication to confirm its validity.
- To better recognize and resist spear phishing and phishing assaults, educate yourself and others about them.
- Inform the appropriate authorities of any suspicious emails, texts, or social media posts.
How Skysnag can protect your organization from Spear-phishing and Phishing attacks.
As phishing continues to increase, you must ensure your domain is well-protected. Your recipients should only get emails sent or authorized by you. And the best way to do this is by automating DMARC.
Create a Skysnag account here to generate your DMARC record
Protect your domain from any phishing attacks with strict DMARC enforcement, all autonomously with Skysnag. Get started with Skysnag and sign up using this link for a free trial today.