The Skysnag Blog
Your destination for the latest in email security and compliance - featuring expert guidance, product updates, and practical resources.
Phishing and Cyber Threats
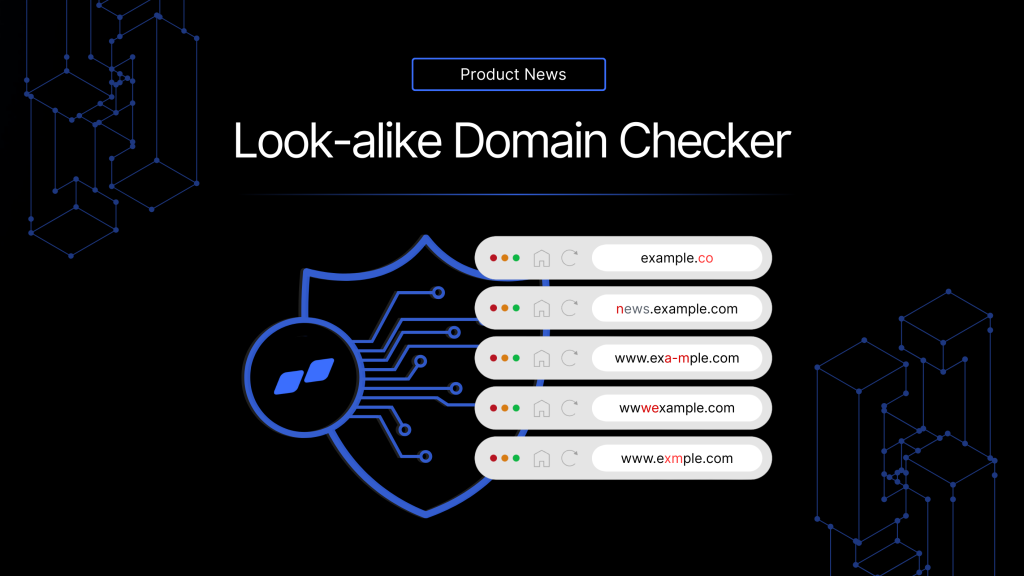
Skysnag Releases Look-Alike Domain Checker to the Public
Phishing and Cyber Threats
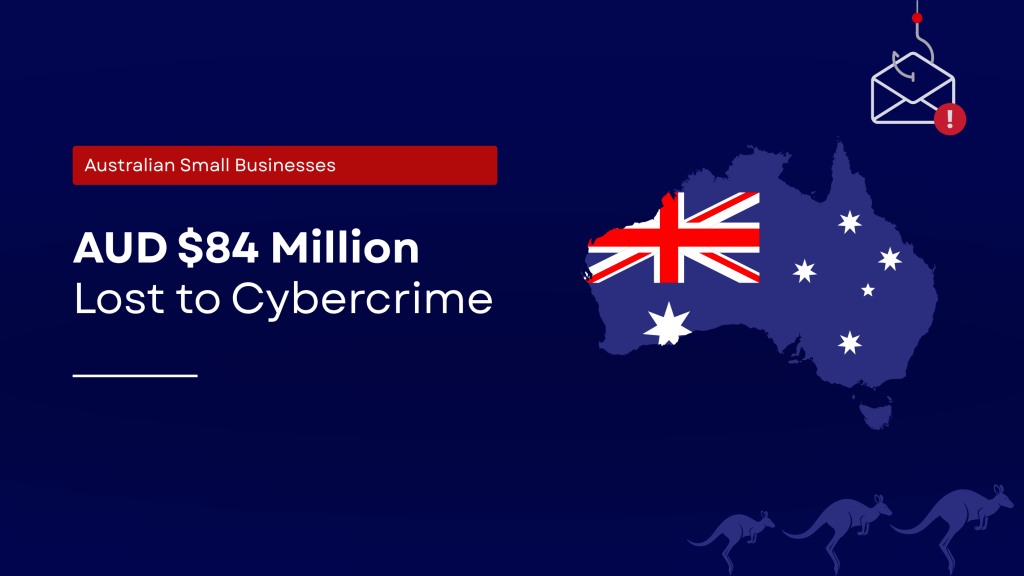
Small Businesses in Australia Face $84 Million in Cyber Losses: What Went Wrong?

Email Authentication and Standards
Why Businesses Should Automate DMARC: Compliance, Security, and Control

Phishing and Cyber Threats
The Business Email Compromise (BEC) Protection Guide

Featured
Skysnag Brings Automated DMARC to Microsoft Customers
Email Deliverability and Best Practices
Phishing and Cyber Threats
Compliance and Regulatory Mandates
Looking for more?