If DMARC is required, why is it not used?

DMARC (Domain-based Message Authentication, Reporting, and Conformance) is an email validation system that prevents your company’s email domain from being used for email spoofing, phishing scams, and other cybercrimes. Which leads us to ask how much is DMARC required?
The email authentication methods Sender Policy Framework and DKIM are used with DMARC. Reporting is a crucial service that DMARC adds. A domain owner will learn who is sending email on their behalf when they publish a DMARC entry in their DNS record. Your domains can be safeguarded with DMARC against misuse in phishing or spoofing attacks.
What is DMARC and why is it required?
There are nearly 4.26 Billion email accounts already existing worldwide, making it easier for cybercriminals to use them for harmful purposes. Despite the efforts of many security agencies, the amount of crime across this channel is increasing every year. The DMARC requirement comes into effect at this point. DMARC not only offers a thorough insight into email activity but also recognizes all forms of email phishing attacks. Among other things, DMARC can lessen the impact of phishing and malware assaults, lessen spoofing, guard against brand abuse, and prevent scams.
How is the DMARC record implemented?
To use DMARC, a legitimate DMARC record needs to be published. The DMARC record is shown, tested, and verified as legal using Skysnag’s free DMARC Record Checker tool. You may verify the DMARC status of your domain by entering the domain name and clicking check DMARC.
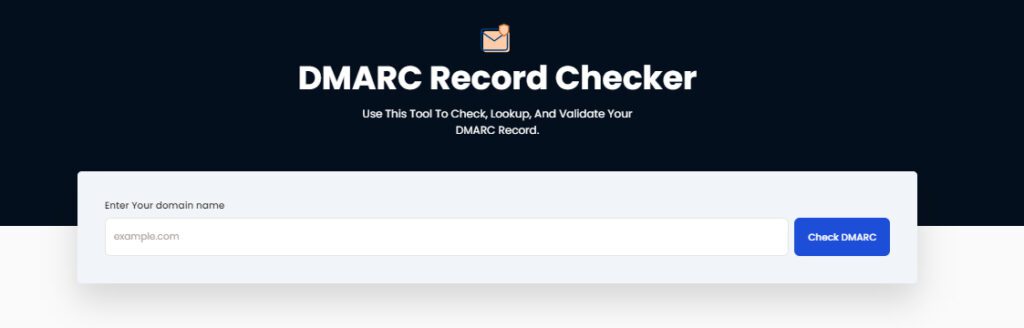
The DMARC Record Checker will additionally look to see whether any foreign domains are being used.
So what makes it so challenging to deploy DMARC.
Why is it challenging to deploy DMARC if it’s required?
SPF and DKIM, for example, are two more email authentication standards that DMARC uses. However, an email message that passes SPF and DKIM validation may still fail DMARC authentication. This is because DMARC requires SPF and DKIM addresses to be “aligned” with the human-readable “From” address, which is a crucial step in preventing fraud. The non-matching authentication result is simply rejected in circumstances where SPF or DKIM authenticates with an identity whose domain does not match the domain in the human-readable “From” address, and the message will fail DMARC authentication. This results in deploying DMARC even harder.
The SPF lookup limit is another issue. A receiving mail server may have to perform one or more DNS lookups as part of determining if an email message passes SPF authentication. Only the first ten DNS lookups are assessed to prevent denial of service attacks. Companies with more than 10 lookups in their SPF records will have problems, because messages may fail authentication if the stated domain arrives too late in the list.
Misconceptions about DMARC
There are a few misconceptions about DMARC. Here are some of the most typical:
I have to set up DMARC for each sender.
Wrong. Since DMARC is a consistent method of email delivery, you only need to configure it once. For all of your outgoing emails, if you run a business, you only need to configure your DMARC record once.
To utilize DMARC, I must have SPF and DKIM configured.
This misperception is typical. Actually, even with SPF or DKIM configured only, you can still use DMARC. The best course of action is to combine DMARC with SPF and DKIM.
To set up DMARC, I need a domain.
Yes. To configure DMARC, you need a domain name.
Create a Skysnag account to generate your DMARC record.
Conclusion
Skysnag’s automated DMARC solution strengthens protection against phishing and spoofing by confirming that an email message came from the domain it claims to have come from. Skysnag generates DMARC reports for you that aid in investigating potential security problems and identifying potential risks from impersonation attacks. Get started with Skysnag and sign up using this link.