What is Whaling? and how to prevent it?
As cyberattacks develop, more sophisticated methods of data breach are affecting a lot more businesses. Due to the COVID-19 pandemic and the fact that most businesses now operate remotely, phishing assaults have increased drastically. According to Google, during COVID-19 an estimated 240 million phishing-related emails were blocked during this time.
So what is Whaling? Let’s find out in this article.
What is Whaling? and how does it work?
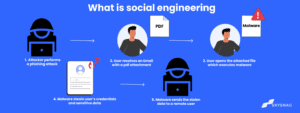
A whale attack is a type of phishing attack that targets high-profile executives, such as the CEO or CFO, with the goal of stealing critical information from a business. The purpose of many whale phishing attempts is to trick the victim into approving high-value wire transfers to the attacker through social engineering, email spoofing and content spoofing efforts.
How does it work?
Scammers examine an organization’s public documents and social media to build a profile and then launch a targeted assault. It could consist of an email from the CEO or another senior executive.
Such an email also contains information that gives the impression that it comes from a reliable source. Because a high-level member has more powers and trust inside their organization, scammers usually go above and beyond to make the scam appear genuine.
What are the impacts of a Whaling Attack?
Data loss
Corporate networks can become infected with malware by clicking a link or downloading an attachment from an email. This may lead to data breaches, such as the theft of intellectual property or the loss of client information.
Financial loss and reputational damage
A whaling assault can cause significant financial or data loss, which can be very embarrassing for both an organization and a person. The CEO of the Austrian aerospace business FACC, who in 2016 suffered a €50 million loss as a result of a targeted email attack, was fired along with other staff employees.
How to prevent Whaling Attacks
Maintain the Privacy of Sensitive Information on Social Media
It should be simple to impersonate a high-level executive. On the internet, there is frequently a wealth of information on them. Top executives should keep their information as private as possible on social media.
Conduct security awareness training.
This attack style frequently targets senior executives. However, for the whaling attack to be successful, the email must appear authentic. Senior leaders and staff must receive training from organizations on how to recognize and avoid cybersecurity dangers.
Consult the sender first before acting
The victim’s reaction to urgency is a key component of one of the most popular whaling techniques. The attacker typically sends an email with a critical request in it. This prompts the recipient to act without first verifying. Skysnag automates DMARC, DKIM, and SPF protocols automatically verifying whether or not an email is genuine.
Conclusion
Whaling attacks cause exponentially larger losses due to their association with high-profile executives. To prevent this Skysnag’s automated software safeguards your domain’s reputation and keeps you away from compromised business emails, password theft, and potentially significant financial losses. Sign up using this link for a free trial and protect your business from Whaling Attacks.