What is social engineering
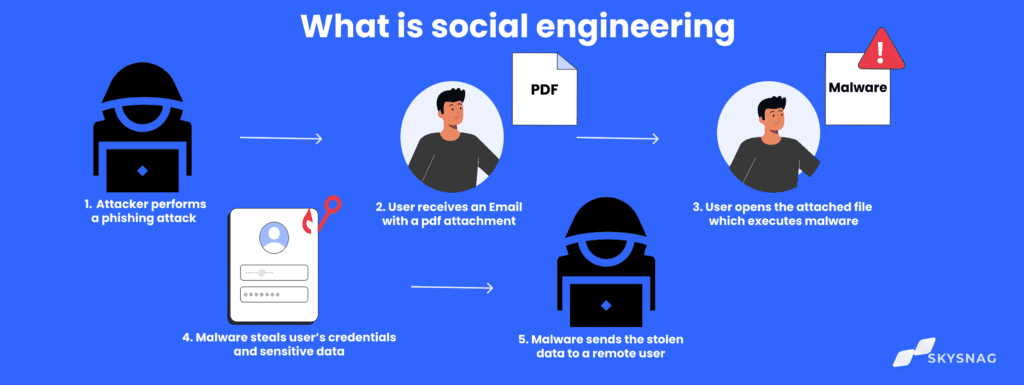
Social engineering is a security attack that relies on human interaction to trick users into breaking standard security procedures. Attackers use social engineering techniques to manipulate people into divulging confidential information, such as passwords or bank account numbers.
History of Social Engineering
Social engineering has been around for centuries, but the term wasn’t coined until the 1980s. One of the earliest documented social engineering attacks was the 1851 Great Gold Hoax, in which two men convinced people in San Francisco that they had found gold in the Sierra Nevada mountains. The men sold shares of their “mining company” and made off with the money.
Types of Social Engineering
There are many different types of social engineering attacks, but we will look at the 10 of the most used attacks:
1. Phishing
Phishing is a type of social engineering attack that uses email or text messages to trick users into clicking on a malicious link or attachment. attackers will often pose as a trusted entity, such as a bank or government organization, in order to gain the victim’s trust. Once the victim clicks on the link or attachment, they will be redirected to a malicious website or their computer will be infected with malware.
2. Pretexting
Pretexting is a type of social engineering attack where the attacker creates a false scenario to obtain personal information from the victim. For example, an attacker may pose as a customer service representative and call a victim to “verify” their account information. The attacker will then use the victim’s personal information to access their accounts or commit other crimes.
3. Baiting
Baiting is a type of social engineering attack where the attacker leaves a physical device, such as a USB drive, in a public place. The device will usually contain malware or a malicious link. When the victim finds the device and plugs it into their computer, their system will be infected with malware.
4. Quid Pro Quo
Quid pro quo is a type of social engineering attack where the attacker offers the victim something in exchange for personal information or access to a system. For example, an attacker may pose as an IT support representative and offer to “fix” a victim’s computer in exchange for their remote access to the system. Once the attacker has access to the system, they can then install malware or steal sensitive information.
5. Dumpster Diving
Dumpster diving is a type of social engineering attack where the attacker rummages through trash bins or dumpsters to find sensitive information that has been discarded. This information can be used to access systems or commit other crimes.
6. Shoulder Surfing
Shoulder surfing is a security attack where the attacker observes a victim entering their password or PIN into a computer or ATM. The attacker can then use this information to access the victim’s accounts or commit other crimes.
7. Tailgating
Tailgating is a type of social engineering attack where the attacker follows a victim into a secure area, such as an office building or parking garage. The attacker can then gain access to the victim’s accounts or commit other crimes.
8. Vishing
Vishing is a type of social engineering attack that uses voice calls or text messages to trick victims into divulging sensitive information. The attacker will often pose as a trusted entity, such as a bank or government organization, in order to gain the victim’s trust. Once the victim provides the attacker with the requested information, the attacker can then use it to gain access to the victim’s accounts or commit other crimes.
9. Watering Hole
The watering hole is a type of social engineering attack where the attacker compromises a website that the victim frequents. The attacker can then infect the victim’s computer with malware or steal sensitive information when visiting the website.
10. Whaling
Whaling is a security attack that targets high-profile individuals, such as CEOs or celebrities. To gain the victim’s trust, the attacker will often pose as a trusted entity, such as a bank or government organization. Once the victim provides the attacker with the requested information, the attacker can use it to gain access to the victim’s accounts or commit other crimes.
Social Engineering tactics
There are many tactics that social engineers use to trick their victims, but some of the most common are:
- Impersonation: These cybercriminals will often pose as a trusted individual, such as a customer service representative, in order to gain the victim’s trust.
- Authority: They will often use their position of authority to convince victims to comply with their requests.
- Intimidation: Social engineers will sometimes use intimidation tactics, such as threatening to terminate a victim’s account, to get them to comply with their demands.
- Flattery: Cybercriminals will often try to flatter their victims to gain their trust.
- Scarcity: They will often create a sense of urgency by claiming a limited product or service supply.
Examples of Social Engineering Attacks
- The 2017 Equifax Breach
In 2017, the credit reporting agency Equifax suffered a data breach that exposed the personal information of over 140 million people. The attackers used a type of social engineering attack known as phishing to gain access to Equifax’s systems. Once the attackers had access to the systems, they could steal sensitive information, such as Social Security numbers and credit card numbers.
- The 2016 US Presidential Election
In 2016, the Russian government used social engineering attacks to interfere with the US Presidential election. The attackers used a type of phishing attack to gain access to the email accounts of Hillary Clinton’s campaign chairman, John Podesta. The attackers then released the contents of the emails to the public to damage Clinton’s presidential campaign.
- The 2017 WannaCry Ransomware Attack
In 2017, the WannaCry ransomware attack affected over 200,000 computers in 150 countries. The attackers used a social engineering attack known as phishing to trick victims into clicking on a malicious link. Once the victims’ computers were infected with the ransomware, the attackers demanded a ransom to decrypt the files.
- The 2018 Facebook Data Breach
In 2018, the social media giant Facebook suffered a data breach that exposed the personal information of over 87 million people. The attackers used a social engineering attack known as phishing to gain access to Facebook’s systems. Once the attackers had access to the systems, they were able to steal sensitive information, such as names, email addresses, and phone numbers.
- The 2018 Instagram Hack
In 2018, the photo-sharing app Instagram was hacked, and the personal information of over 6 million users was exposed. The attackers used a social engineering attack known as phishing to gain access to Instagram’s systems. Once the attackers had access to the systems, they were able to steal sensitive information, such as names, email addresses, and phone numbers.
What are the 6 steps to a Successful Social Engineering Attack
- Research: The attacker researches the target organization and its employees in order to collect as much information as possible.
- Planning: The attacker plans the attack, taking into consideration the information they have gathered in the research phase.
- Execution: The attacker carries out the attack, using the methods and techniques they have planned.
- Delivery: The attacker delivers the payload, which could be malware, sensitive information, or credentials.
- Control: The attacker takes control of the system or account, using the information or access they have gained.
- Cover-up: The attacker covers their tracks, making it difficult to detect the attack and trace it back to them.
FAQs
How does social engineering work?
Social engineering is a type of attack that relies on human interaction to trick users into breaking standard security procedures. The attacker works to gain the user’s trust and then uses that trust to get the user to do something that will allow the attacker to gain access to the system.
How Severe is Social engineering?
While social engineering can be used to achieve various goals, it is most often used to gain access to systems or data. Once an attacker has access to a system, they can exploit it for their own gain. This can result in data loss, financial loss, and even damage to the system.
What is the most common type of Social Engineering
One of the most common types of social engineering is phishing. This is where an attacker sends an email that appears to be from a legitimate source, such as a bank or a website. The email will contain a link that will take the user to a fake website designed to look like the real thing. The user is then asked to enter their login details, which the attacker can use to gain access to the system.
How can I prevent Social Engineering?
There are a few things that you can do to help prevent security attacks. First, you should be aware of the dangers of clicking on links in emails. If you are unsure about the source of an email, you should not click on any links contained within it. Second, you should never give out personal information, such as your login details, to anyone who you do not know and trust. Finally, you should always keep your systems up to date with the latest security patches to help prevent attackers from exploiting any vulnerabilities.
What percentage of hackers use social engineering
Social engineering is a popular technique among hackers, estimated to be used in around 90% of successful attacks.
What is the cost of a social engineering attack?
The average social engineering attack costs an organization $1.6 million and takes 4 months to detect. A significant portion of this cost is due to the fact that it is difficult to determine when an employee falls victim to an attack. Any employees with legitimate access can leave the environment vulnerable to attackers when they fall for a social engineering campaign and install malicious software, provide credentials to attackers, or divulge sensitive information.
How to Protect your business from Social Engineering Attacks
Skysnag automates DMARC, SPF, and DKIM for you, saving you the trouble and time required for manual configuration. Skysnag’s automated software safeguards your domain’s reputation and keeps you away from compromised business emails, password theft, and potentially significant financial losses. Sign up using this link for a free trial and protect your business from social engineering attacks.