P=none DMARC
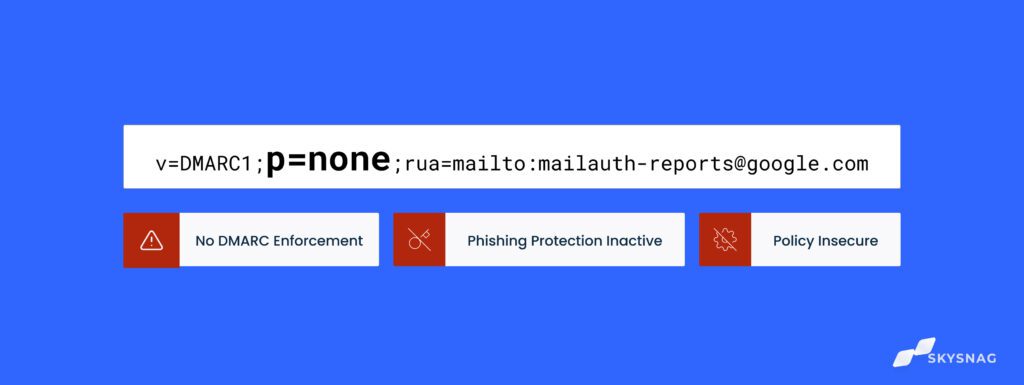
Having a DMARC record set to p=none is essentially equivalent to not having a DMARC record at all. Without enforcement (p=none), it is similar to having an access management system that scans IDs but allows anyone to enter, even if the ID scan results in an unidentified individual. The DMARC policy identified with a “p” is the most crucial part of DMARC enforcement because it gives domain owners the ability to specify how they want to handle emails that fail authentication checks. With DMARC enforcement (p=reject), domain owners can instruct email clients to send unauthenticated messages to the spam folder or block them entirely.
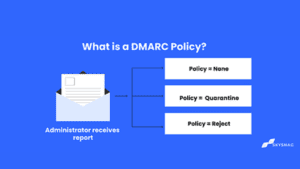
What are the DMARC policies?
DMARC policies allow domain owners to specify what they want to happen with emails that fail SPF and DKIM authentication checks.
- p=none — No enforcement; mail that fails authentication is typically delivered.
- p=quarantine — Messages that fail authentication are delivered to spam.
- p=reject — Messages that fail authentication are blocked by mail clients and not delivered. Some receivers honor this request, while others mark failing messages as spam.
The policy p=none is a monitoring mode policy that does not provide any enforcement, leaving a domain vulnerable to spoofing. This policy is commonly used in test mode to troubleshoot authentication misconfigurations with third-party senders, without the risk of blocking legitimate emails.
To prevent phishing and impersonation attacks, it is necessary to set DMARC to enforcement (p=quarantine or p=reject), rather than p=none.
In p=none mode, domain owners can utilize the reports sent by mail clients to identify the IP addresses attempting to exploit their domain by sending fraudulent emails. The information provided in these reports should be transformed into actionable insights in order to achieve p=reject for the domain, which is the actual technical challenge.
Unfortunately, the majority of companies that attempt DMARC fail to reach enforcement. Approximately 80% of companies with a published DMARC record are not set to p=reject. This can be attributed to misconfiguration issues, reliance on limited reporting tools that do not enforce DMARC, or encountering technical challenges with their email senders.
Risks a company faces with no DMARC enforcement
Email impersonation/spoofing: With a policy of p=none, attackers can impersonate a domain name without any restrictions. This allows anyone to use the domain name to send emails, posing a significant risk to customers, partners, and other stakeholders. Potential risks include:
- Financial loss
- Reputation damage
Emails landing in spam: without DMARC enforcement, internet service providers are unable to determine whether messages pass or fail authentication, resulting in messages being classified as spam.
Create a Skysnag account to generate your DMARC record.
With the domain being vulnerable to email impersonation and attackers having free access to use the domain, email clients may begin flagging the domain. This can lead to adverse long-term consequences, such as the domain being placed on a blacklist. Being blacklisted disrupts mail delivery, resulting in undelivered mail, and it can take up to 3-4 weeks to have the domain removed from the blacklist.
What happens if no action is taken?
In cases of severe unauthorized usage, mail clients can go beyond classifying emails as spam and may choose to blacklist the domain name. When a domain is blacklisted, it leads to emails being blocked from reaching the majority of mail clients.
Skysnag, as the first DMARC enforcement solution on the market, eliminates the laborious DNS process associated with email authentication protocols. It achieves this by transforming the records into dynamic formats rather than static DNS records. As a result, businesses can autonomously enforce this email loophole, saving valuable hours of engineers’ time.